SSH keys on Windows with PuTTY
In this post we will be covering getting up and running with Putty on Windows to work with Git repositories and accessing Linux machines using SSH keys.
If you already have an SSH key you can jump to Loading your key in Pageant.
[!WARNING] Never share you private keys with anyone.
Getting up and running
Install the PuTTY suite using Chocolatey
choco install -y putty
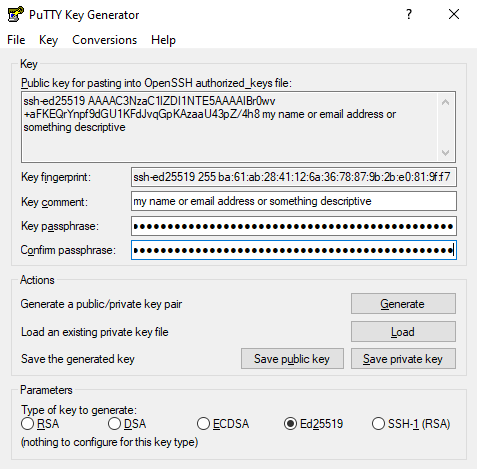
Start puttygen to generate your key.
![]()
Make sure to select the key type ‘Ed25519’ in the bottommost part of the screen.
(If you really need an older RSA key, you can generate that as well afterwards, but don’t use it as your default key.)
Click ‘generate’ and move the mouse around to help generate some randomness.
Make sure to fill out the ‘Key comment’ and add a passphrase after they key is created.
Note that the ‘Public key’ and the ‘Key fingerprint’ will be different each time you generate a key.
Next, click in the ‘Save private key’ and save it to a directory only you have access to on your local computer. This will save it in the ‘PuTTY Private Key Files’ format which has a ‘.ppk’ file ending, needed with pageant. You can call it putty_id_ed25519.ppk, usernameyyyy_putty_id_ed25519.ppk or whatever you want.
[!WARNING] Never share you private keys with anyone.
Content of a .ppk file. As this private key will never be used, it’s ok to show it. But never try this with your private keys at home kids.
You can identify it as a private key from the ‘Private-Lines’ section.
PuTTY-User-Key-File-2: ssh-ed25519
Encryption: aes256-cbc
Comment: my name or email address or something descriptive
Public-Lines: 2
AAAAC3NzaC1lZDI1NTE5AAAAIFwKPm7sBEZtcfew1Nm4KlR8eOZpdc/mjB2SFGju
/VkC
Private-Lines: 1
EvIEgnc6Exz/OONY8avVoQSBuZudDi/6GoQZhmJAg70i9DNmO0IDzMr9XV4zm0sT
Private-MAC: f9f39de3a2b4a51c641b927aa099cc1ab2292ee2
Next copy the content in the ‘Public key for pasting into OpenSSH authorized_keys file:’ box, open up and editor and save it as id_ed25519.pub, usernameyyyy_id_ed25519.pub or whatever you want. Make sure the file is saved with LF file endings. If possible, as that will matter on a Linux system. Windows file ending is CRLF. Called ‘End of Line sequence’ in Visual Studio Code.
Content of a public key. This content is ok to share.
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFwKPm7sBEZtcfew1Nm4KlR8eOZpdc/mjB2SFGju/VkC my name or email addrtess or something descriptive
We have yet to come acress a need for this public key format that Puttygen offers, but you can also save the public key by clicking the ‘Save public key’. Make sure you distinguish that this is the public key exported from putty by calling it putty_id_ed25519_pub or similar (there is no .ppk as it’s not a private key).
Content of a public key. This content is ok to share. Note that this differs from the public key that shows up in the Puttygen window.
You can identify it as a plublic key by, you guess it, the ‘---- BEGIN SSH2 PUBLIC KEY ----’ section.
---- BEGIN SSH2 PUBLIC KEY ----
Comment: "my name or email addrtess or something descriptive"
AAAAC3NzaC1lZDI1NTE5AAAAIFwKPm7sBEZtcfew1Nm4KlR8eOZpdc/mjB2SFGju
/VkC
---- END SSH2 PUBLIC KEY ----
You can also go in under the ‘Conversions’ menu and choose ‘Export OpenSSH key’.
The default private key names on Linux are id_ed25519 or id_rsa, with the corresponding public keys as id_ed25519.pub and id_rsa.pub. But you can name them anything. Just make sure to remember which is which.
This is for when you need to use the private key from a Linux machine.
Content of a SSH private key file. As this private key will never bee used, it’s ok to show it.
You can identify it as a plublic key by, the ‘-----BEGIN OPENSSH PRIVATE KEY-----’ section.
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABBv
srX5osvcyyViA1NKNXvpAAAAEAAAAAEAAAAzAAAAC3NzaC1lZDI1NTE5AAAAIFwK
Pm7sBEZtcfew1Nm4KlR8eOZpdc/mjB2SFGju/VkCAAAAoBno8uQEcpfZQEA8BIBS
FZit3Ie9Jpvmz8GQbj0cEqAFX4YKnd75m1zq9fiYhqVWoIBCB+qTIsc2cWQwvCpp
jkzKrBUJVbNpzhvwYWvO998R7FQ5PhXa+OYwKpN8NzZ3d4nNEDbXxvXAd1O4LPn8
psLO+dYJTXKWYIfxW3FxUfjMR7ajPK/rFrd2eZeSA5dJrCt+ZBUQ5k/CD8vp7v1A
PBc=
-----END OPENSSH PRIVATE KEY-----
We are now done with creating keys. Let’s load em’ up.
Loading your keys in Pageant
Launch pageant, which should show up down in the lefthand corner as a tray icon.
![]()
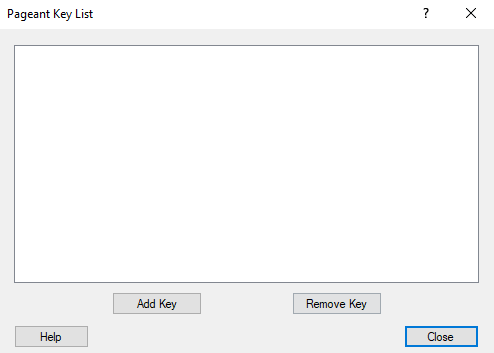
From the Pageant Key List window you can see any loaded keys and also add or remove them.
Click ‘Add Key’ to load your .ppk key. As indicated before Pageant can only read .ppk files. All keys loaded will show up in the list.
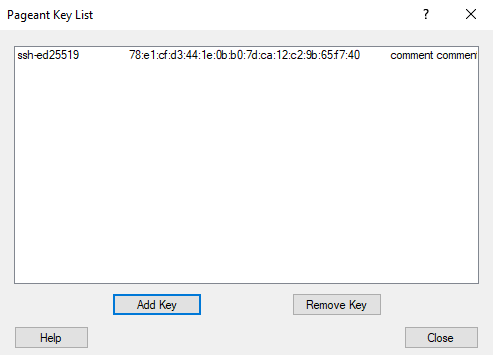 You have to do this each time you start your computer and Pageant will keep the key(s) in memory for as long as you’re logged in on your computer. Just make sure to lock your workstation when you leave it as you always do.
You have to do this each time you start your computer and Pageant will keep the key(s) in memory for as long as you’re logged in on your computer. Just make sure to lock your workstation when you leave it as you always do.
Add your public key to Gitlab
Copy the contents of the id_ed25519.pub file
Login to Gitlab and navigate to settings -> SSH Keys
Paste the key in, the Title section will be auto populated with your key comment but you can adjust that as needed.
Troubleshooting
These steps might be required. Should perhaps be turned into a separate blog post one day.
You might need to add a Windows environmental variable so that git understands do use plink, the PuTTY equivalent of the cli command ssh to enable loaded Pageant keys to to work fully in Windows, if that is not done already.
Open up powershell as your own user and paste the following. Closing the current powershell window and opening another one might be required after the command.
[Environment]::SetEnvironmentVariable("GIT_SSH", "C:\ProgramData\chocolatey\bin\PLINK.EXE", "User")
For gitlab specific, it might also be nessecary to add Gitlabs public ssh key. You can do that by running this command from a normal user powershell and pressing control + c when you see the login as: prompt.
PS C:\temp> plink gitlab.com
The server's host key is not cached in the registry. You
have no guarantee that the server is the computer you
think it is.
The server's ssh-ed25519 key fingerprint is:
ssh-ed25519 255 2e:65:6a:c8:cf:bf:b2:8b:9a:bd:6d:9f:11:5c:12:16
If you trust this host, enter "y" to add the key to
PuTTY's cache and carry on connecting.
If you want to carry on connecting just once, without
adding the key to the cache, enter "n".
If you do not trust this host, press Return to abandon the
connection.
Store key in cache? (y/n) y
login as:
That is all folks.
Make sure to also check out our blog post on how to work with SSH keys on Ubuntu.
Make sure to always keep your Operating System(s) and all of the software that you are using up to date.
Feedback on our content or did you find a bug somewhere?
Send us an email to feedback at this domain.
kthxbai